Durex Condom Online Data Breach
On 5th March 2010, I discovered a data breach on the Durex India website Kohinoor Passion. I had earlier ordered Durex products off their estore, and my order had arrived by courier in a nondescript shipping package as promised. Later, I passed an eye over the invoice enclosed with my order. I noticed that it appeared to have been printed off a website, since the url of the website was printed at the bottom of the invoice. Since my computer was switched on and connected to the internet at the time, I idly entered the url in my browser, and received a surprise when my invoice came up on screen, looking exactly as printed – showing my name, contact information, products ordered and amount invoiced.
I considered that my login to the Durex estore might still have been alive from my shopping session, and so tried again after clearing my browser history, cache and cookies. For good measure, I even restarted my computer. I could still access my invoice online.
Now my curiosity was piqued. I noticed that my order number was part of the url, and so randomly changed this number. To my amazement, another invoice came up, with the order details of someone else who had ordered Durex products online at the estore.
Each Durex estore invoice looks something like this:
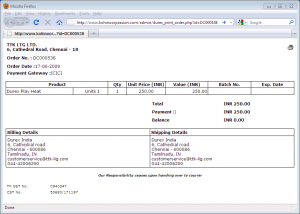 Now replace the billing and shipping details with actual online shoppers’ names, postal and email addresses, and phone numbers, and you’ll realize the enormous amount of information that was at an unsecured location, freely available to anyone with a connection to the internet. (The main admin page http://www.kohinoorpassion.com/admin/ required a username and password, but apparently the subpages didn’t.)
I immediately starting emailing the following people (using my real name and email address) informing them of the breach:
13:39 TTK-LIG Customer Service (TTK-LIG is the marketer of the Durex brand in India)
14:49 SSL International Open Door (SSL is the owner of the Durex brand worldwide)
20:22 Lisa Caton, Consumer Relations Manager at SSL (I received a vacation response)
20:29 Garry Watts, Chief Executive at SSL
20:50 Paul Doherty, Head of Corporate Affairs at SSL
20:54 Consumer Relations at SSL
When I went to bed, the data breach was still active, and more invoices seemed to have been added that day.
When I checked the next morning, the website had been modified, and any direct invoice access attempts redirected to the admin login page. Although I appreciated the speed taken to solve the problem, especially on a weekend, it is anyone’s guess how long the data breach was active before I discovered it, or how many customer records were accessed in that time from unauthorized locations.
Now replace the billing and shipping details with actual online shoppers’ names, postal and email addresses, and phone numbers, and you’ll realize the enormous amount of information that was at an unsecured location, freely available to anyone with a connection to the internet. (The main admin page http://www.kohinoorpassion.com/admin/ required a username and password, but apparently the subpages didn’t.)
I immediately starting emailing the following people (using my real name and email address) informing them of the breach:
13:39 TTK-LIG Customer Service (TTK-LIG is the marketer of the Durex brand in India)
14:49 SSL International Open Door (SSL is the owner of the Durex brand worldwide)
20:22 Lisa Caton, Consumer Relations Manager at SSL (I received a vacation response)
20:29 Garry Watts, Chief Executive at SSL
20:50 Paul Doherty, Head of Corporate Affairs at SSL
20:54 Consumer Relations at SSL
When I went to bed, the data breach was still active, and more invoices seemed to have been added that day.
When I checked the next morning, the website had been modified, and any direct invoice access attempts redirected to the admin login page. Although I appreciated the speed taken to solve the problem, especially on a weekend, it is anyone’s guess how long the data breach was active before I discovered it, or how many customer records were accessed in that time from unauthorized locations.
